![]() I agree. Maybe remove the IPV6 from your DNS, or figure out why your hosting provider is intercepting IPV6 traffic (at least that’s what I assume based on screenshots below). That would prevent Let’s Encrypt from validating.
I agree. Maybe remove the IPV6 from your DNS, or figure out why your hosting provider is intercepting IPV6 traffic (at least that’s what I assume based on screenshots below). That would prevent Let’s Encrypt from validating.
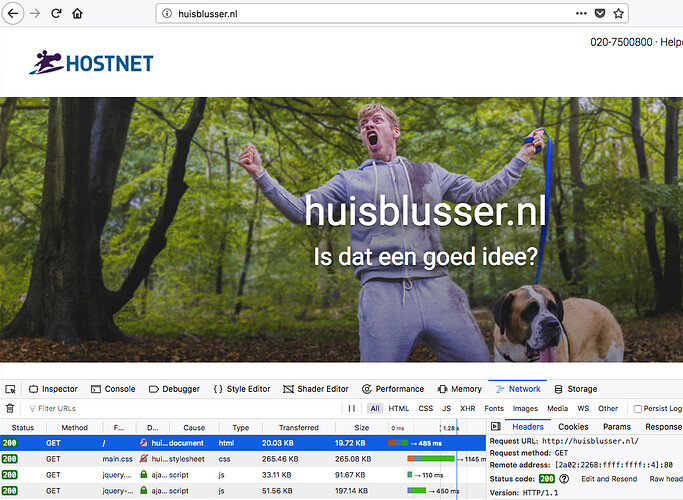
huisblusser.nl from IPV6:
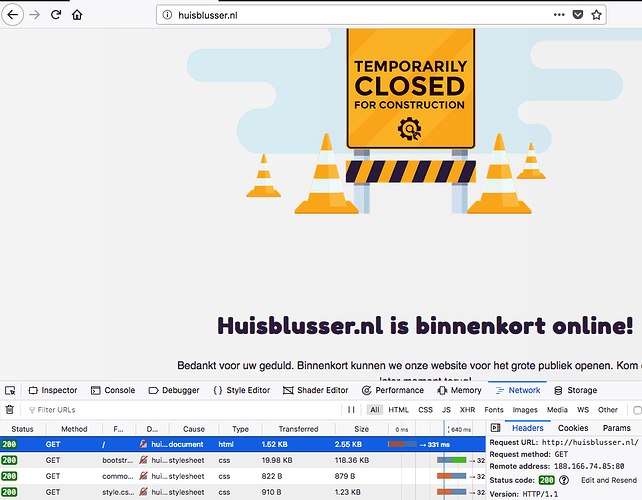
huisblusser.nl from IPV4:
# IPV6 acme challenge gives 404
curl -6 -s -o /dev/null -w "response %{http_code} from %{remote_ip}" http://huisblusser.nl/.well-known/acme-challenge/vbU-ncuUumk1a3Cx5g55xE8LjJTfduJxE9GkFzH7WQA
response 404 from 2a02:2268:ffff:ffff::4%
# IPV4 acme challenge gives 200
$ curl -4 -s -o /dev/null -w "response %{http_code} from %{remote_ip}" http://huisblusser.nl/.well-known/acme-challenge/vbU-ncuUumk1a3Cx5g55xE8LjJTfduJxE9GkFzH7WQA
response 200 from 188.166.74.85%
# IPV6 server: Apache
$ curl -6sI http://huisblusser.nl | grep Server
Server: Apache
# IPV4 server: nginx
curl -4sI http://huisblusser.nl | grep Server
Server: nginx
Note: I think Trellis should work fine with serving IPV6 traffic, but there isn’t yet as much security for IPV6